- Filter by
- Categories
- Tags
- Authors
- Show all
- Announcements
- Cyber Security
- Enhancements & Fixes
- Information Security
- Malwares
- Mobile Security
- Security
- Social Media
- Tech Trends
- Upgrades
November 16, 2017
Published by Solomon Komen at November 16, 2017
Categories
How can we apply Business Processes Automation (BPA) and Cyber Security to ensure food security and solve major problems faced by young farmers, new farmers, large […]
September 7, 2017
Published by Solomon Komen at September 7, 2017
Internet provides an opportunity for all to learn new things, do business, connect with interesting people, contribute on trending topics and to be part of good […]
July 17, 2017
Published by Solomon Komen at July 17, 2017
Kenya is on the top 20 list of countries most affected by spam calls, a majority of which are originated by fraudsters, caller ID application TrueCaller […]
May 16, 2017
Published by Solomon Komen at May 16, 2017
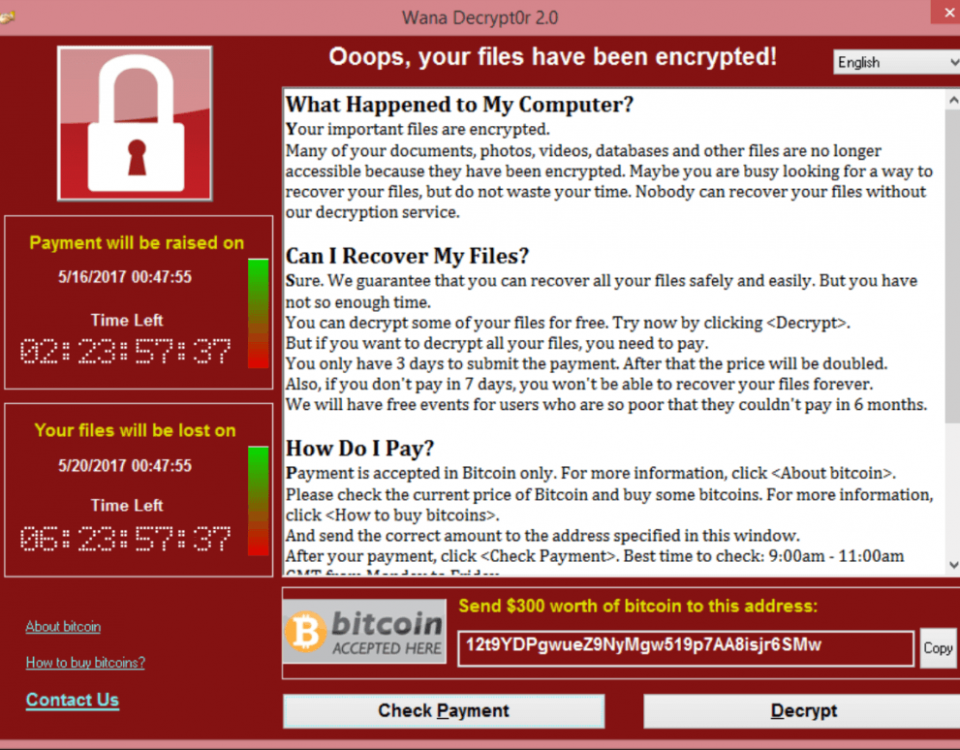
Currently, there is no WannaCry decryption tool or any other solution available, so users are strongly advised to follow prevention measures in order to protect themselves. […]
April 19, 2017
Published by Solomon Komen at April 19, 2017
A PC without an antivirus installed and running will likely be infected within minutes of connecting to the internet. An ounce of prevention beats a pound […]
February 20, 2017
Published by Solomon Komen at February 20, 2017
Categories
If you have an android phone you must be feeling pretty secure with its best feature, the pattern lock. The pattern lock system is used among […]
February 17, 2017
Published by Solomon Komen at February 17, 2017
Categories
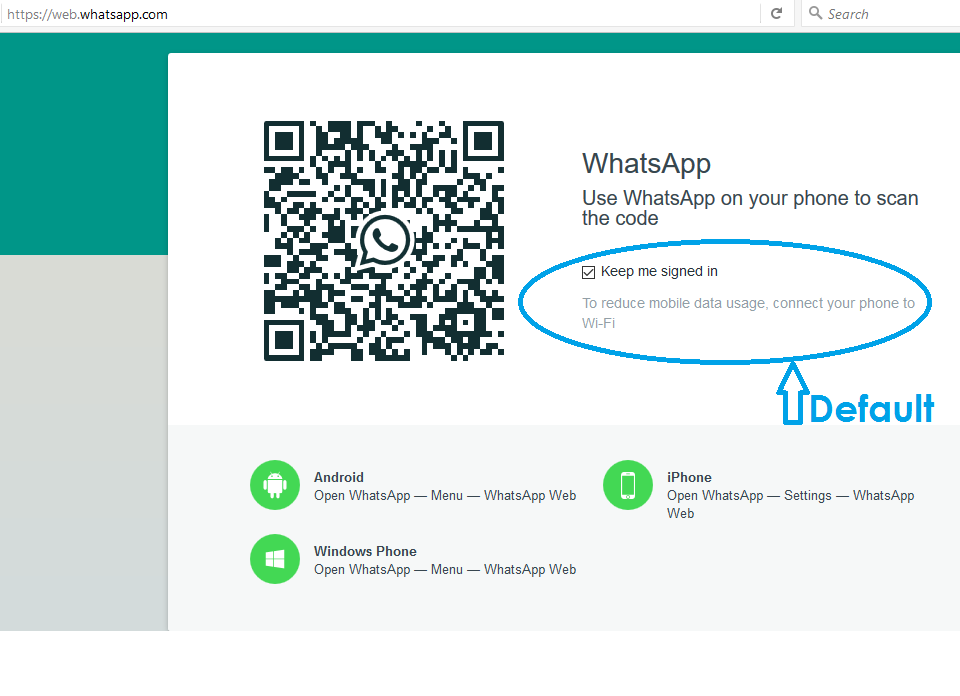
WhatsApp is now accessible both on your phone and your computer and someone could be reading and even be seated somewhere responding to your WhatsApp messages […]
February 13, 2017
Published by Solomon Komen at February 13, 2017
Categories
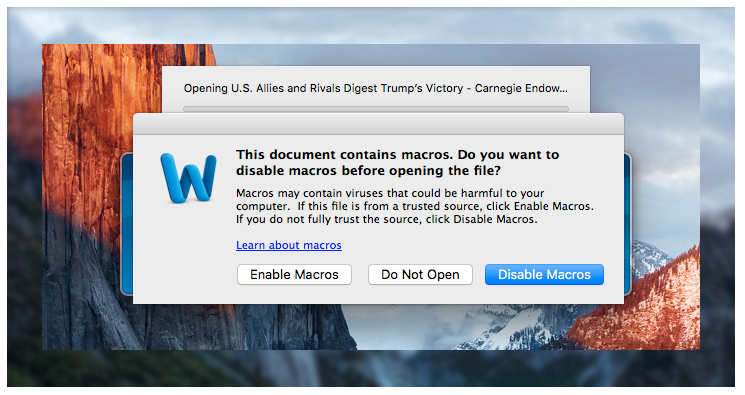
After targeting Windows-based computers over the past few years, hackers are now shifting their interest to Macs as well. The emergence of the first macro-based Word […]
February 3, 2017
Published by Solomon Komen at February 3, 2017
Categories
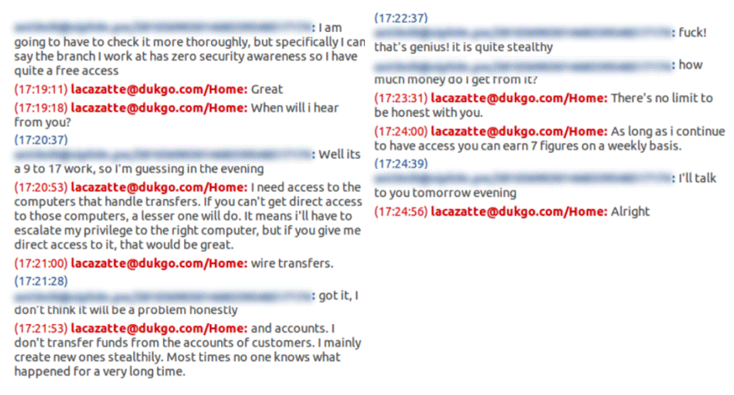
Besides selling their company’s secret information, researchers also found evidence of rogue staff, in some cases, even working with hackers to infect their company networks with […]
February 1, 2017
Published by Solomon Komen at February 1, 2017
Categories
Without doubt, mobile devices, especially smartphones have become our best friends. We use them to make calls, take photos, shop online, bank, store personal or office […]